Wifi Hacking WPA/WPA2 with Kali Linux
Warning..!! WIFI hacking is illegal.
“This article is only for educational purposes. We are not responsible for any consequences.”
Now, let's get started...
There are 3 types of security in Wifi :
WEP stands for WIRED EQUIVALENT PRIVACY
- Encryption key of either 64 bits or 128 bits in HEX.
- The flaws in WEP make it susceptible to various statistical cracking techniques.
- If we can capture enough number of the IVs, we can decipher/decrypt the key !
- DES Encryption, which is easy to break
WPA stands for WIFI PROTECTED ACCESS
- It builds upon WEP, to make it more secure by adding extra security mechanism and algorithms to stop unauthorized access.
- WPA delivers a level of security way beyond anything that WEP can offer.
- It's a new security standard adopted by the WiFi Alliance.
WPA2 Wifi Protected Access with AES
- The primary difference between WPA and WPA2 is that WPA2 uses a more advanced encryption technique called AES (Advanced Encryption Standard)/ccmp
- We prefer WPA2 because it has more secure from these three protection levels, making it nearly impossible for computer guru hackers to break the encryption. AES is so good that it blocks statistical analysis of the cipher text. WPA2 is based upon the Institute for Electrical and Electronics Engineers’ (IEEE)
As WEP is outdated and rarely seen, so we will crack WPA and WPA2.
What we are going to do:
# Capturing WPA packets# Capturing Handshake
# Wordlist
#cracking
Tools, which we'll use in this:
1.airmon-ng2.airodump-ng
3.aireplay-ng
4.aircrack-ng
All of them are preinstalled in kali linux. One of the best operating system for hacking. Have all the tools required for hacking preinstalled in it.
Note: If you are using kali in vmware, you'll need a device i.e, an External Wireless Adapter for capturing the packets.
Now lets start WPA/WPA2 password cracking:
1. Disconnect from all wireless networks. You can either be in a wireless network or can enable monitor mode.Both can't be done at same time.
Type airmon-ng
This command will show the available wifi cards that can enable monitor mode .
In this case our wireless interface is wlan0.
What is monitor mode ?
monitor mode allow a computer with a Wireless Network Interface Controller(WNIC) to monitor all traffic received from wireless network.
2.Now type airmon-ng start wlan0
This command will start the monitor mode.
see the second last line:
(mac80211 monitor mode vif enabled for[phy0]wlan0 on [phy0]wlan0mon)
It is also showing the process that can cause problem.Just ignore it.
So now our monitor mode is enabled.
3. If i again type airmon-ng you can see my interface is shifted to wlan0mon as seen in last step .
4. Type airodump-ng start wlan0mon.
This command start the capturing of all the traffic.This include information of all wireless access points that are available around you.
This is the result of airodump command.
Once you see your target network stop dumping the traffic using ctrl+c.
Lets understand the important terms first:
a).BSSID: This is the mac address of the router.
b).Beacons: These are the packets broadcasted by the router to show its availability.more the baecons more near is the router.
c).Data: These are the data packets that travel between authenticated clients and router that show users connected to a router is doing something on the internet.
d).Channel(ch):On which channel frequency router is broadcasting.It can be different or same for different routers and not fixed for any routers.A router can shift between channel 1 to 13.
e).ENC:It is the type of security that a router has.
f).ESSID:Name of the wifi.
Now we select your target . In this case i have selected Tenda which has WPA security on it.Same method can be applied to crack WPA2 security.
5.open another terminal and type
airodump-ng -c[channel] --bssid[bssid] -w /root/Desktop/mukul [ monitor interface ]
#Replace channel with the channel of your target in this case it is 6.
#Replace bssid with the bssid (Mac Address) of the router you are attacking in this case it is C8:3A:35:D7:91:18.
# -w /root/Desktop/mukul "mukul" is the file name.
The “–w” and file path command specifies a place where airodump will save any intercepted 4-way handshakes (necessary to crack the password). Here we saved it to the Desktop, but you can save it anywhere.
6.
Now we have to wait for the 4 way handshake to occur.
Means we have to wait until a device to makes connection or reconnection with the router.This can take a variable amount of time and is unreliable method.
This is where aireplay-ng comes into picture.
What we are going to do is ,we will force a client connected to the router to reconnect with the router by sending deauthentication packets to the client . This will make the device think like it has to reconnect with the router.
Note: For this tool to work there must be some device connected to the router.
7.
The highlighted text are the BSSID (router's mac address) and STATION(client's mac address that is connected with the router).
8.Open another terminal and type the command
aireplay-ng -0 15 -a[bssid] -c[client's mac address] [monitor interface]
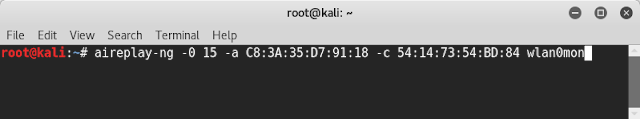
Here -0 enables deauth mode.
15 is the no. of deauth packets to be send.You can send any no. of deauth packets.
Replace bssid with bssid of the targeted router. In this case it is C8:3A:35:D7:91:18.
In -c type the clients bssid(mac address) . in this case i have already highlighted .i.e 54:14:73:54:BD:84.
In this case my monitor interface is wlan0mon.
9.
As you can see aireplay-ng is sending 15 deauth packets.
After it send the asked no. of deauth packets which in this case is 15 you will see WPA handshake:C8:3A:35:D7:91:18 . Bingo! handshake captured.
You will see 4 files created in Desktop (remember the path -w /root/Desktop/mukul). this was the path of the captured handshake.Out of 4 files .cap contains the password that we are seeking.
11.Open another terminal and type :
aircrack-ng -a2 -b[bssid] -w[path to wordlist] /root/Desktop/.cap
-a is the method aircrack will use to crack the handshake, 2=WPA method.
Replace bssid with bssid of the targeted router. In this case it is C8:3A:35:D7:91:18.
-w /usr/share/wordlists/rockyou.txt is the path of the inbuilt wordlist stored in kali.If you have never used it before you have to unzip it using gunzip .
Wordlist are basically the list of passwords. rockyou.txt is of 148 MB. Guys 148 mb text file is huge. Generally we use text file having size in kbs.
There are various wordlist available on internet . You can download them.
There is even a wordlist of 28 GB.You can also download it.
/root/Desktop/.cap is the place where our handshake is stored. In this case .cap file is mukul-01.cap. '-01' in .cap file is added automatically .
Now what aircrack-ng is going to do it picks each password from wordlist encrypt it using the same encryption that password in handshake is having and compare both of them.
The thing is we cannot decrypt the encrypted password in captured handshake.
so aircrack-ng encrypt the each password with same encryption that password in capured handshake is having and compare them.
As you can see KEY FOUND! [ swimmer8 ].
password is swimmer8
This method does not 100% guarantee that it will crack the password. As it depend upon the type of password and capacity of wordlist .
But larger the size of wordlist more are the chance of cracking the password. But on the other hand it takes more time .
How to prevent your password from being cracked :
Always remember wherever you put password like facebook, gmail, wifi etc
- Add special characters.
- add numbers.
- add uppercase and lowercase characters.
- try to make its length long.
- use phrases instead of just words.
like:
# MyCatNameisMisty@123
# phasesmakespasswordssecure!56
# iloveindia(@@@@@)
And there is a very good website on which you can verify the complexity and security of your password.
https://howsecureismypassword.net/

















Post a Comment